Introduction
The streaming services and the food delivery apps that people rely on nowadays for their seamless experience and real-time updates are the benefits we should thank the Cloud for. The development of Cloud is a total game-changer for businesses, providing them with platforms to move with incredible speed and easy scale-up. However, just as every advantage has a drawback, Cloud comes with its own set of associated risks. The exact speed, scalability, and seamless experiences it enables can introduce hidden vulnerabilities that open doors for attackers to exploit. As Cloud adoption is on the rise, data breaches are also increasing. It is therefore essential to examine the Cloud landscape, identify potential threats, and outline measures that can support businesses in the long run through trusted cloud security services.

(Image Source: Cloud Security)
Cloud Security by the Numbers: Risks You Can’t Afford to Ignore
The numbers speak with a clarity that doesn’t need embellishment. They echo what many experienced security leaders have sensed for years: the risks are climbing to levels not seen before, and the fallout from them is growing more serious. Taken together, the figures below outline figures draw a realistic picture of where things stand today.
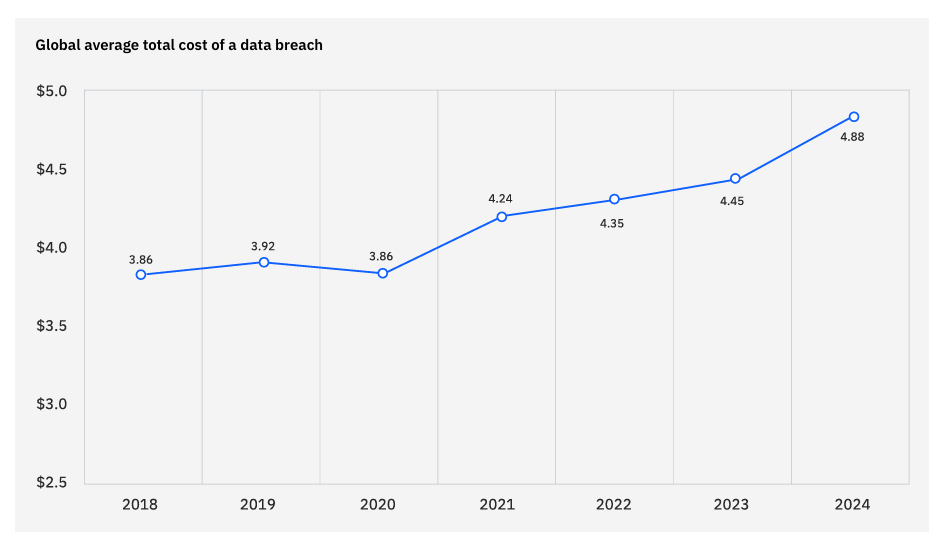
(Image Source: IBM Data Breach Report 2024)
- Data breaches have become incredibly expensive, with the average cost hitting a massive $4.88 million globally last year.
- A staggering 82% of breaches involved data stored in the Cloud, and 39% of those breaches spread across multiple cloud environments.
- Reflecting this growing risk, the cloud security tools market is estimated to grow significantly, possibly reaching a value of about USD 37 billion by 2026 as businesses invest heavily.
Why Cloud Security is Your Business’s Best Insurance
As the numbers show how critical a threat can be for a business, now let’s uncover the “Why” perspective of these risks. The truth is that cloud security isn’t just a technical chore that the IT team is whole sole responsible for handling. It’s the backbone of business strategy. Without it, everything a business has built up, the systems, the reputation, and the customers’ trust can vanish overnight.
It’s easy to dismiss a cyberattack as just an “IT Problem,” but its impact echoes in every domain of the business. Suddenly, salaries might be late, customers can’t log into their accounts, and support lines are completely overwhelmed with calls. If a breach is not noticed at the earliest, then the damage keeps getting worse, and cleaning up the mess costs way more than preventing it ever would have. Good security, when it’s done right, doesn’t just reduce risk; it builds customer trust, and that gives a company a serious advantage over its competitors.
The Top 6 Cloud Threats That Define Modern Risk Landscape
Cloud security is a big deal, but what needs to be protected? The threat landscape has changed. Today’s threats aren’t just simple; they’re always a step ahead to exploit the complex nature of cloud systems. The six significant challenges faced in the industry are:
- Smarter and More Customised Threats: The once simple threats, such as phishing emails and basic malware, are now longer this simple, but with the emerging technology like automation, they have become more innovative and more sophisticated in nature. It’s harder to detect at times!
- Identity and Access Management (IAM) Complexity: Managing who gets access to what in the cloud has gotten really complicated, especially for businesses that are juggling multiple cloud platforms. It’s a tricky environment to navigate. The biggest worries usually come down to a few key things: keeping a close eye on accounts with high-level permissions, dealing with weak or insecure login methods, and sorting out poorly configured access controls.
- Data Protection and Privacy Risks: In Cloud Platforms, data travels constantly between different regions, across various borders, and even between cloud providers, which potentially raises the risks of data exposure to the wrong persons, for businesses if not properly handled.
- Misconfigurations of Cloud Resources: This is one of the most common threats; something as simple as leaving a storage bucket open to the public or failing to set the proper firewall rules can expose sensitive data. As attackers actively scan for such weaknesses.
- Shortage of Skilled Cloud Security Professionals: Around the world, there is a huge scarcity of skilled cloud security professionals. Businesses are heavily adopting cloud services, but the right workforce with the right skills to secure this environment has not grown at the same pace.
- Supply Chain Exposure: Businesses heavily rely on third-party vendors, SaaS applications, and APIs to run their businesses. And these integrations can introduce hidden vulnerabilities. Attackers wait for such weak links in the supply chain.
The Six Best Solutions to the Cloud Security Threats
These complex threats can be overwhelming, but they can be solved. The ever-expanding threat landscape needs proactive strategies to mitigate them. Here’s how enterprises can respond to the top threats and build a robust defence:
- Smarter and More Targeted Threats: To combat smart and specific threats, we need to employ safety measures such as Zero Trust Security by continuously verifying users, devices, and workloads, deploying AI-driven security tools for detection, and constantly conducting employee awareness training instead of assuming.
- Identity and Access Management (IAM) Complexity: Again, as discussed above, implementing the Zero Trust model, Principle of Least Privilege, and Role-Based Access Control helps in streamlining permissions, and also continuous monitoring and audits help in reducing the chances of a threat occurring.
- Protecting Data and Privacy: To keep data protected, businesses can implement data encryption, adopt cloud-native key management services (KMS), can use data loss prevention (DLP) solutions to prevent and detect unauthorized data transfers and ensure alignment with regulations like GDPR, CCPA, etc.
- Misconfigurations Still Lead to Breaches: To overcome misconfigurations, one can use automated cloud security posture management (CSPM) tools to continuously scan for misconfigurations and perform regular red team exercises and penetration testing to uncover weaknesses before attackers do.
- A Shortage of Cloud Security Expertise: To overcome this shortage, businesses can train and invest in employees for training and certification, and embed automation and AI-powered tools to reduce human error and save time. Also, cross-training between IT, DevOps, and security teams can help.
- Supply Chain Exposure: To reduce it, businesses should do proper risk assessment and security questionnaires before integration to assess third-party vendors, and should enforce strict API security measures. Continuous monitoring of third-party activity should be done.
Final Words
Just as great power brings great responsibility, the Cloud carries its own set of obligations. Today, making cloud security less of an expense and more of an insurance policy for protecting customer trust. This article has covered the why perspective, the significant challenges, and the strategies of Cloud adoption. A move to the Cloud is not a risk to fear, but a transition that requires readiness and planning. By implementing proper techniques such as employee training, Zero Trust principles, and automation, business systems stay safe and the ability to grow, innovate, and most importantly, gain customers’ trust also increases.
If your organisation is looking to strengthen its cloud security posture or needs guidance on where to begin, contact Artan for tailored support and practical security solutions.

