Introduction
Cybersecurity has a language of its own, and sometimes it can feel overwhelming. Terms like vulnerability scanning, penetration testing, and VAPT (Vulnerability Assessment and Penetration Testing) often get thrown around as if they mean the same thing. The truth? They do not.
Each approach serves a unique purpose in protecting systems, data, and networks. Understanding the differences is useful not only for security experts but also for students, IT professionals, business owners, and anyone interested in how organisations stay safe online.
This article explains each method in clear language, shares vital statistics, brings in real-world examples, and shows when you might use one or a mix of all three.

(Source: Gemini)
Why These Assessments Matter
The evolving threat landscape is only getting tougher:
- The global average cost of a data breach reached USD 4.88 million in 2024, up from USD 4.45 million in 2023.
- Research shows that 67% of organizations will face at least one cyberattack related to their digital transformation efforts.
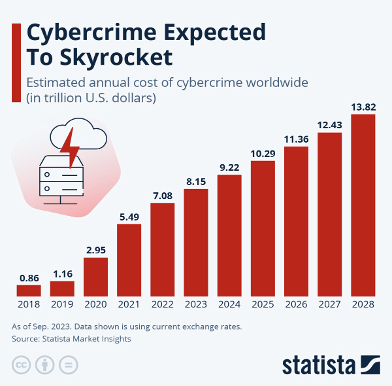
(Source: Statista)
- The Global cost of digital crime is projected to increase from USD 9.22 trillion in 2024 to USD 13.82 trillion by the year 2028
- 37% of organizations reported budget cuts in their cybersecurity departments in 2024.
These numbers show why “hoping for the best” is not a good approach. Regular checks must be performed to stay ahead of attackers.
Vulnerability Scanning: The First Line of Defence
Think of vulnerability scanning as a health check for your systems. It is an automated process that scans computers, networks, and applications to find weaknesses.
- What it does: Looks for missing software patches, weak settings, and known flaws.
- How it helps: Gives you a list of problems ranked by severity.
- Strengths: Fast, automated, covers much ground.
- Limitations: Can flag false positives and cannot confirm if attackers could really exploit the issue.
Example: A retail business uses scanning tools weekly. They identify an outdated web server component before attackers can exploit it. The IT team patches the issue within 24 hours, preventing what could have become a serious compromise.
In short, scanning is excellent for spotting potential problems quickly, but it does not tell the whole story.
Penetration Testing: The Real-World Drill
Penetration testing, or pen testing, is like using ethical hackers to break in and see what is really possible.
- What it does: Goes beyond lists, showing how an attacker can chain issues together to get inside.
- How it helps: Provides a real-life view of what could happen if vulnerabilities are ignored.
- Strengths: High accuracy, business context, practical insights.
- Limitations: Slower, more expensive, usually done once or twice a year.
Example: A healthcare provider undergoes a penetration test. Testers exploit a weak password reset function and an outdated API, gaining access to patient data. The exercise highlights critical flaws, leading the provider to enforce stronger authentication, patch the API, and improve monitoring to protect sensitive records.
If vulnerability scanning is like a doctor’s check-up, pen testing is like a stress test; it shows how systems perform under pressure.
VAPT: The Complete Picture
VAPT (Vulnerability Assessment and Penetration Testing) combines the breadth of scanning with the depth of pen testing.
- What it does: First scans for vulnerabilities, then tests the most serious ones to confirm real-world risk.
- How it helps: Gives both visibility and proof, which is essential for compliance (ISO 27001, PCI DSS, SOC 2).
- Best for: Organisations that want a full assurance of security, not just a partial view.
Example: An e-commerce company preparing for PCI DSS certification uses VAPT. The assessment not only finds issues but also validates them. Auditors receive evidence of due diligence, customers gain trust, and the business achieves compliance more smoothly.
Think of VAPT as the all-in-one package: it tells you what is wrong, then shows how it could play out in practice.
Quick Comparison: Vulnerability Scanning vs Penetration Testing vs VAPT
| Aspect | Vulnerability Scanning | Penetration Testing | VAPT |
| Definition | Automated scan for known issues | Simulated attack by ethical hackers | Combination of both |
| Approach | Broad, automated | Focused, manual + tools | Hybrid |
| Depth | Surface-level | Deep, real-world | Broad + deep |
| Goal | Find vulnerabilities | Prove risks | Full assurance |
| Output | List of issues | Attack narrative & fixes | Combined validated report |
| Cost/Time | Low/Fast | Higher/Slower | Highest/Most thorough |
How to Use Them Together
One of the biggest mistakes is thinking you need to choose only one. In reality, the strongest security programmes use all three methods in combination.
- Start with vulnerability scanning: Run scans weekly or monthly. It gives constant visibility, which is crucial as new flaws appear daily.
- Add penetration testing: Carry out at least once a year, or after significant system changes (new applications, cloud migrations, mergers). It validates your defences in real-world conditions.
- Adopt VAPT: Use it when preparing for external audits, certifications like ISO 27001 or PCI DSS, or when reporting to stakeholders who expect evidence of both breadth and depth.
Best Practice: Document all your findings, track improvement progress, and revisit the assessments regularly. Security is not a single event but an ongoing cycle.
Final Words
There is no single solution that can guarantee security. Absolute protection comes from combining different approaches. Vulnerability scanning is helpful in uncovering possible weak spots in your systems. Penetration testing goes further by demonstrating how those weaknesses could be used in an attack. VAPT offers the most complete view, bringing both methods together to show a clear picture of your risks.
It makes no difference if you are a student learning the basics, an IT professional managing systems every day, or a business leader responsible for compliance. Understanding these approaches is essential for anyone with an interest in cybersecurity. Regular assessments are not just technical tasks; they are part of building resilience, meeting compliance standards, and maintaining customer trust. Because threats continue to evolve, security cannot be treated as a one-off project. Organisations that make scanning, penetration testing, and VAPT part of a regular cycle are not only strengthening their defences today, but also protecting their reputation and long-term future.
For organisations looking to strengthen their assessment approach, you may contact Artan for guidance tailored to your environment.

